A note to casual visitors. All of the exercises on this web site were performed ethically and not against any actual users. All of the machines are virtual machines that I have set up on my device for training purposes only. The virtual machines that I am using are Kali Linux, and Metasploitable 2 which is a deliberately vulnerable workstation that is used for training purposes. The networks are also isolated internal networks that are virtual as well. Never under any circumstances perform any of these demonstrations on actual users without their full permission! If you are interested in learning about ethical hacking there are tons of resources available. Some of it is free, and some of it you have to purchase or subscribe to. I will be posting a resource page in the future containing some of my favorite places to learn ethical hacking as well as IT training. My reason for choosing this demonstration is to show potential job recruiters that I have an understanding of a combination of topics such as networks, virtualization, TCP, vulnerability scans, the CVE database, and more.
Nmap and Wireshark Demonstration
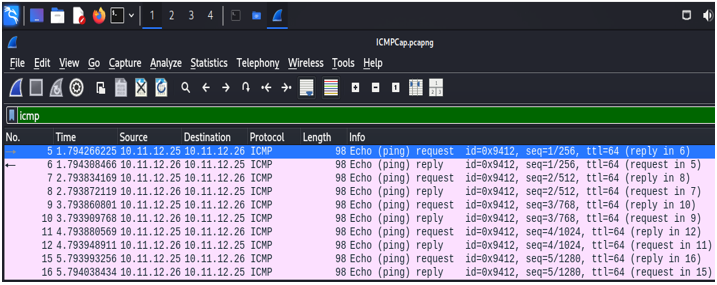
This screenshot shows a basic ICMP or ping command being used. While it is normal to sometimes see ICMP on the network, an excessive amount can indicate the beginning of a Denial of Service attack.
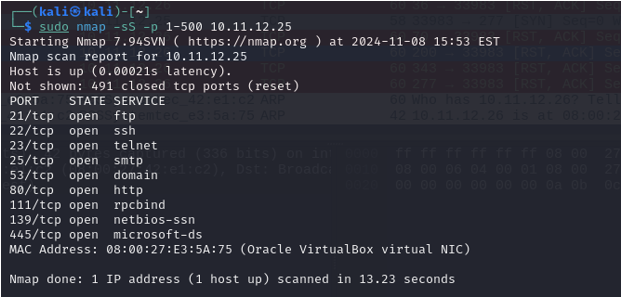
In this scan, I have used the Nmap SYN scan also known as a stealth scan on ports 1-500 against Metasploitable 2. This scan will use SYN packets to determine if a port is open. The scan has determined that several ports are open. The SYN scan will be discussed in further detail on the next image.
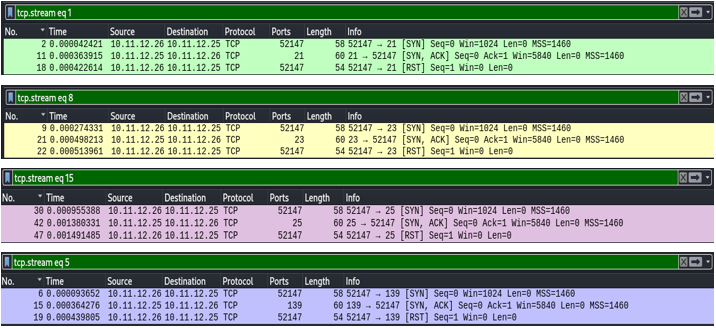
This image shows the SYN scan captured in Wireshark. An indication that a SYN scan is taking place is that a large amount of SYN packets will be sent within a small time-frame on several ports. Also observe the three stages of the scan. The TCP handshake is not completed. Instead, a RST packet is sent to close the session and move on to the next port.
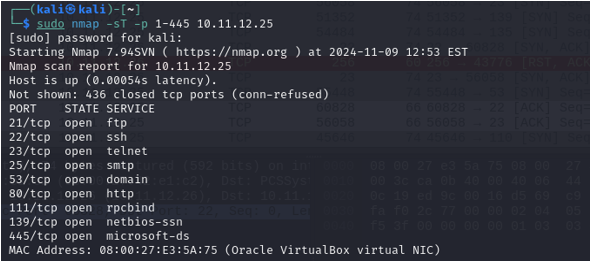
The type of Nmap scan that was used here is a full TCP connection scan. Rather than ending the TCP handshake pre-maturely with a reset flag, the entire handshake is completed on each port using SYN, SYN ACK, ACK.
This capture shows the complete handshake being performed on a few ports before moving on to the next one. As you can see, the three-way handshake is being completed on each port. [SYN] [SYN, ACK] [ACK]
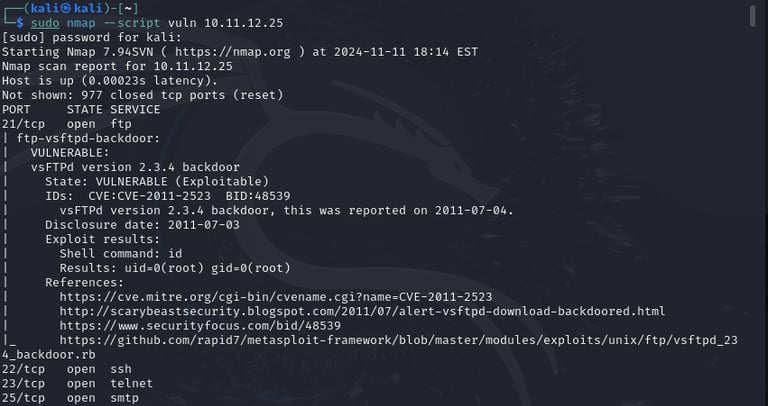
This screenshot shows a vulnerability scan that was performed against the Metasploitable 2 machine. This is only a partial screenshot. There are many more vulnerabilities present on this virtual machine. This type of scan is very useful and informative. The scan gives a description of each vulnerability as well as the CVE ID where further research of each vulnerability can be done on the CVE database website.
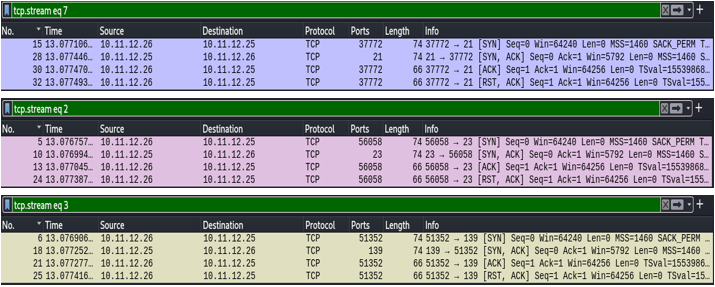
The following Nmap scan is the ACK scan. This scan is often used to test for a stateful firewall by determining if a port is filtered. If the port is unfiltered, the target machine will respond with a RST packet. If the port is filtered, the machine will not respond or a destination unreachable message will be received. Notice the machine gave a reset response indicating the ports are unfiltered.
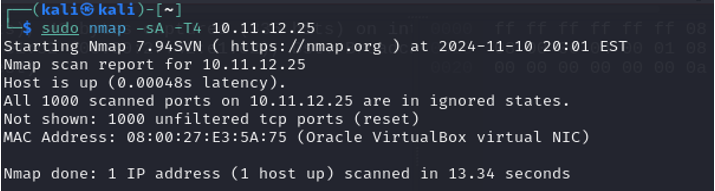
The following capture is the Metasploitable 2 machine. Notice the RST reply for each unfiltered port that was scanned.

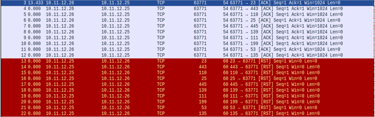
For comparison, the following scan was performed on my Windows 10 virtual machine with the firewall activated. Notice that the machine gave no-response indicating the ports have been filtered.


This is the Windows 10 machine that was scanned with the firewall activated. Notice there are no RST replies from the ports.

